
pengantar
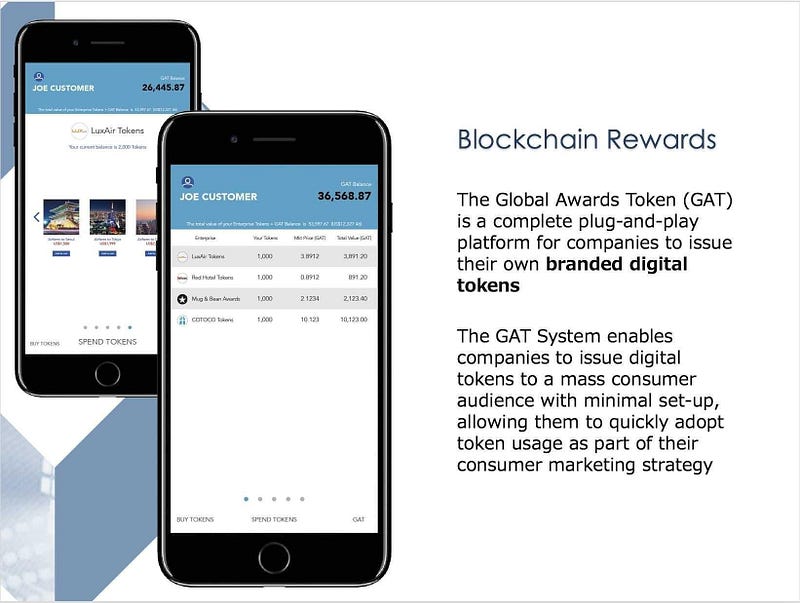
Koin GAT adalah pedagang terkemuka global untuk menerbitkan sendiri token bermerek digital (Token Pedagang). Sistem GAT memungkinkan perusahaan untuk mengeluarkan token digital ke khalayak konsumen massal dengan minimum set up, yang memungkinkan mereka untuk dengan cepat mengadopsi penggunaan token sebagai bagian dari keseluruhan strategi pemasaran mereka.
Koin GAT akan menjadi mata uang pertukaran eksklusif untuk perdagangan Token Pedagang di Bursa GAT.
Koin GAT adalah pedagang terkemuka global untuk menerbitkan sendiri token bermerek digital (Token Pedagang). Sistem GAT memungkinkan perusahaan untuk mengeluarkan token digital ke khalayak konsumen massal dengan minimum set up, yang memungkinkan mereka untuk dengan cepat mengadopsi penggunaan token sebagai bagian dari keseluruhan strategi pemasaran mereka.
Koin GAT akan menjadi mata uang pertukaran eksklusif untuk perdagangan Token Pedagang di Bursa GAT.
Desain sistem
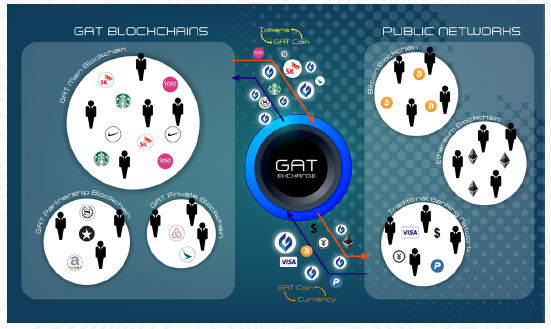
Sistem GAT terdiri dari:
GAT Wallet: dompet token seluler, platform belanja dan portal pembayaran
GAT Marketplace: toko pedagang yang berpartisipasi untuk penjualan dan pembelian produk dengan Token Pedagang
GAT Exchange: token exchange untuk penjualan dan pembelian Merchant Tokens dengan GAT Coin
Jaringan GAT: jaringan konsorsium swasta sof buku besar super besar kecepatan tinggi
di mana Token Pedagang disirkulasikan.
Sistem GAT terdiri dari:
GAT Wallet: dompet token seluler, platform belanja dan portal pembayaran
GAT Marketplace: toko pedagang yang berpartisipasi untuk penjualan dan pembelian produk dengan Token Pedagang
GAT Exchange: token exchange untuk penjualan dan pembelian Merchant Tokens dengan GAT Coin
Jaringan GAT: jaringan konsorsium swasta sof buku besar super besar kecepatan tinggi
di mana Token Pedagang disirkulasikan.
Ringkasan proyek
Intinya, Sistem GAT adalah solusi perusahaan bagi pedagang global untuk menerbitkan token digital mereka sendiri ke khalayak konsumen massal. Proyek ini berusaha menciptakan lingkungan yang terkendali bagi perusahaan untuk menggunakan token digital, sehingga mengurangi hambatan tradisional untuk adopsi blockchain yang dihadapi oleh perusahaan arus utama yang berusaha memanfaatkan inovasi blockchain.
Dalam Sistem GAT, pedagang membuat dan menerbitkan token digital bermerek mereka sendiri yang disebut Token Pedagang. Token Pedagang ditampilkan di dompet token mobile yang didesain dengan indah. Merchant Tokens kemudian beredar di jaringan konsorsium swasta yang hanya bisa diakses oleh perusahaan dan konsumen yang berpartisipasi. Token Merchant kemudian digunakan untuk membeli atau menukarkan produk dan layanan nyata dari merchant yang berpartisipasi.
Intinya, Sistem GAT adalah solusi perusahaan bagi pedagang global untuk menerbitkan token digital mereka sendiri ke khalayak konsumen massal. Proyek ini berusaha menciptakan lingkungan yang terkendali bagi perusahaan untuk menggunakan token digital, sehingga mengurangi hambatan tradisional untuk adopsi blockchain yang dihadapi oleh perusahaan arus utama yang berusaha memanfaatkan inovasi blockchain.
Dalam Sistem GAT, pedagang membuat dan menerbitkan token digital bermerek mereka sendiri yang disebut Token Pedagang. Token Pedagang ditampilkan di dompet token mobile yang didesain dengan indah. Merchant Tokens kemudian beredar di jaringan konsorsium swasta yang hanya bisa diakses oleh perusahaan dan konsumen yang berpartisipasi. Token Merchant kemudian digunakan untuk membeli atau menukarkan produk dan layanan nyata dari merchant yang berpartisipasi.
GATCOIN Bekerja?
A-DropTM memberi kekuatan pengecer yang belum pernah ada sebelumnya untuk membawa pelanggan ke toko dengan hadiah mata uang kripto yang ditargetkan secara geo. Pers menyebut kita sebagai inovasi pemasaran terbesar sejak ditemukannya poin.
A-DropTM memberi kekuatan pengecer yang belum pernah ada sebelumnya untuk membawa pelanggan ke toko dengan hadiah mata uang kripto yang ditargetkan secara geo. Pers menyebut kita sebagai inovasi pemasaran terbesar sejak ditemukannya poin.
GATCOIN menyediakan insentif penjualan yang likuid, dapat diperdagangkan, untuk pasar ritel massal. Kami
adalah platform belanja ritel terdistribusi dimana pedagang manapun
dapat membuat token digital merek mereka sendiri dan menampilkannya
untuk menargetkan pemirsa di manapun di dunia. Token
akan mengganti poin loyalitas tradisional, kupon diskon dan voucher
hadiah, dan bisa diperdagangkan secara bebas di Stok GAT kami.
Teknologi A-Drop Target GATCOIN memungkinkan pedagang mengirimkan token secara digital kepada pelanggan mereka berdasarkan demografi, preferensi belanja dan lokasi geografis. Hal ini memberi peluang kepada pengecer yang belum pernah terjadi sebelumnya untuk menargetkan khalayak secara real-time sebagai pertukaran mata uang kripto nyata untuk perlindungan toko. GATCOIN awalnya akan meluncurkan lebih dari 60.000 + gerai ritel dan 21 merek global utama di Asia pada tahun 2018 melalui program penghargaan sosial Plan Planet Jepang.
Teknologi A-Drop Target GATCOIN memungkinkan pedagang mengirimkan token secara digital kepada pelanggan mereka berdasarkan demografi, preferensi belanja dan lokasi geografis. Hal ini memberi peluang kepada pengecer yang belum pernah terjadi sebelumnya untuk menargetkan khalayak secara real-time sebagai pertukaran mata uang kripto nyata untuk perlindungan toko. GATCOIN awalnya akan meluncurkan lebih dari 60.000 + gerai ritel dan 21 merek global utama di Asia pada tahun 2018 melalui program penghargaan sosial Plan Planet Jepang.

PARAMETER PENJUALAN TOKEN:
1.Tanggal Tanggal: 28 Oktober 2017
2.Token Ditawarkan: 200.000.000 ERC20 GAT Coins
3.Min Funding Goal: US $ 20.000.000
4.Max Funding Cap: US $ 60.000.000
5.Total Supply: 1.000.000.000 tetap, non-inflasi
6.Pendiri Share: 10%, untuk pengembangan lanjutan
7.Share Foundation: 10%, untuk aktivitas market maker
8.Distribusi Masa Depan: 60% selama 3 tahun dari 2018-2021
9. Waktu Tradable: Segera setelah kesimpulan penjualan. GATCOIN sedang dalam diskusi lanjutan dengan pertukaran kripto utama untuk pencatatan Koin GAT untuk segera diperdagangkan setelah penjualan. Pengumuman tertunda
1.Tanggal Tanggal: 28 Oktober 2017
2.Token Ditawarkan: 200.000.000 ERC20 GAT Coins
3.Min Funding Goal: US $ 20.000.000
4.Max Funding Cap: US $ 60.000.000
5.Total Supply: 1.000.000.000 tetap, non-inflasi
6.Pendiri Share: 10%, untuk pengembangan lanjutan
7.Share Foundation: 10%, untuk aktivitas market maker
8.Distribusi Masa Depan: 60% selama 3 tahun dari 2018-2021
9. Waktu Tradable: Segera setelah kesimpulan penjualan. GATCOIN sedang dalam diskusi lanjutan dengan pertukaran kripto utama untuk pencatatan Koin GAT untuk segera diperdagangkan setelah penjualan. Pengumuman tertunda
Solusinya
Kami percaya bahwa banyak, jika tidak semua masalah ini dapat ditangani dengan menciptakan lingkungan yang terkendali di mana perusahaan dapat menerapkan token digital ke khalayak konsumen massal, sehingga mengurangi risiko yang mungkin berdampak negatif terhadap adopsi teknologi, nilai merek, dan masalah peraturan potensial. .
Kami percaya bahwa banyak, jika tidak semua masalah ini dapat ditangani dengan menciptakan lingkungan yang terkendali di mana perusahaan dapat menerapkan token digital ke khalayak konsumen massal, sehingga mengurangi risiko yang mungkin berdampak negatif terhadap adopsi teknologi, nilai merek, dan masalah peraturan potensial. .


Detail informasi


